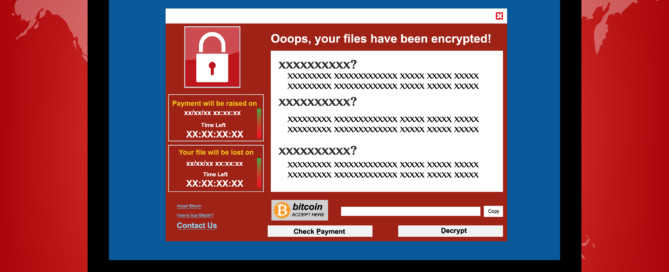
Phantom Extortion Phishing Targeting Financial Services Firms!
Recently a few of our clients were recipients of phishing email leveraging scare tactics, also known as the Phantom Extortion Scam. This scam involves cyber criminals sending fake emails or messages to individuals or businesses, claiming that there has been a security breach or incident involving sensitive client or organization data. The cyber criminals then