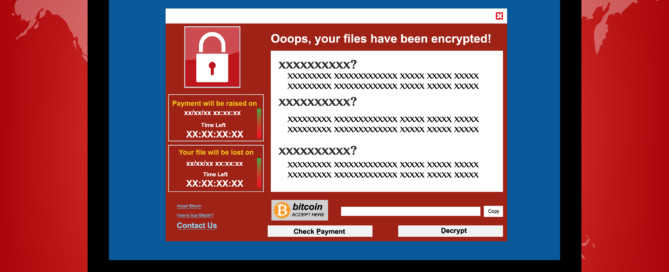
Next Generation Ransomware Attacks
Ransomware, the word alone evokes fear into many companies. How did this form of crime actually start? In 1989, Dr. Joseph L. Popp created the first ransomware called the "AIDS Trojan." This trojan virus encrypted files on a computer after rebooting a number of times. Fast forward to 2006, Archiveus, a computer virus that affected