The team at Check Point identified that cyber criminals – dubbed the Florentine Banker – targeted three Private Equity firms and stole over $1.3 million dollars, with only about half the money recovered.
The cyber criminals launched an email spear-phishing campaign targeting executives, and other high-profile employees in an attempt to gain access to their email account and passwords. Once access was gained, the cyber criminals monitored the activity of the mailbox over several months to learn how the firms operate, who the important people in the firm are, which counter-parties they work with, what deals are currently being worked on, which portfolio companies are requesting funds, etc.
In addition to monitoring the inbox the cyber criminals set up email forwarders to receive copies of emails that contained sensitive information that helped in their attacks, registered similar domain names that were used to spoof both sides of the communication, set up bank accounts, and used money mules to move the money – all amounting to a very sophisticated attack.
You have probably seen news alerts like this all too often and become numb to them. Maybe you are thinking, too bad for those folks; it will never happen to us because we have good processes in place. If you feel this way, make sure to reassess and reconsider your thoughts about this, as these firms may have felt the same exact way your firm does.
Based on the recent phishing tests that we have performed for our clients over the last month, we have seen a big jump in users failing. (the tests are equal in sophistication level as compared to phishing tests run 3-4 months ago.) Given the recent change in the way we have to work, users are working in a different physical and social environment, are preoccupied with other things, etc. They no longer have a colleague that sits next to them that will warn them about a potential email threat, they have 3-4 different things they are juggling, and will mistakenly click on that phishing email after it hits their inbox.
It is more important now than ever to keep our guards up and remain vigilant to do our best in avoiding these situations.
During our publishing of this article, our founder received a phishing email with someone trying to spoof the “HR Department”. They pulled a copy of our logo from Twitter and included it in what appears to be a terrible signature attempt.
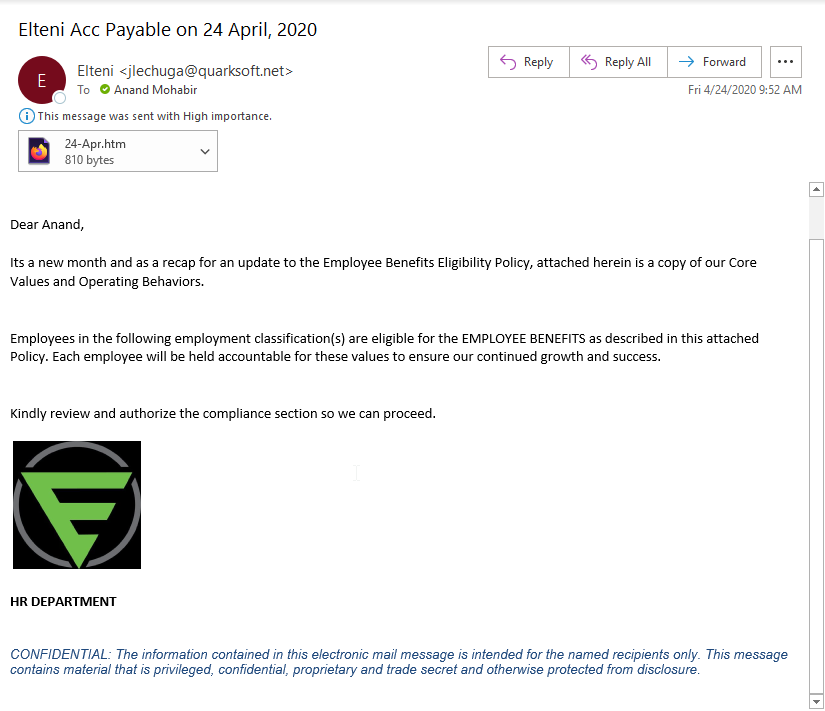
Recommendations
Some things you can do to ensure you are protected.
- Identify all of your entry points into sensitive firm data to identify if sufficient security and monitoring has been applied to detect and/or prevent these types of threats.
- Ensure your configuration of cloud resources are doing exactly what you expect them to do, and no more.
- If you have made exceptions to technical or security policies, make sure you know what your risk exposure is, reconsider the exception, or identify a better solution.
- Make sure all employees are made aware of firm policies and procedures and ensure reviews are being conducted to ensure they are being followed.
- Train your employees, conduct phishing test, voice phishing tests, etc.
Participate in our work from home survey
We understand you are extremely busy and probably have little time for this, but sharing your experiences will not only help others feel socially connected, it will help us all determine the major issues and allows us to solve challenges together. We fully appreciate any time you spend responding to this.
The results of this survey will be shared with all participants.
[button color=”green” size=”large” light=”no” icon=”” open_in_new_window=”yes” link=”https://us18.list-manage.com/survey?u=b7f681478c27a5cb772d5bede&id=6601bb6239″]Take Our Survey Now[/button]



