On January 27, 2020 the Securities and Exchange Commission Commission’s Office of Compliance Inspections and Examinations issued examination observations related to cybersecurity and operational resiliency practices undertaken by market participants.
We reviewed this alert and simplified it into major points that are easily digestible. The OCIE provided the following observations:
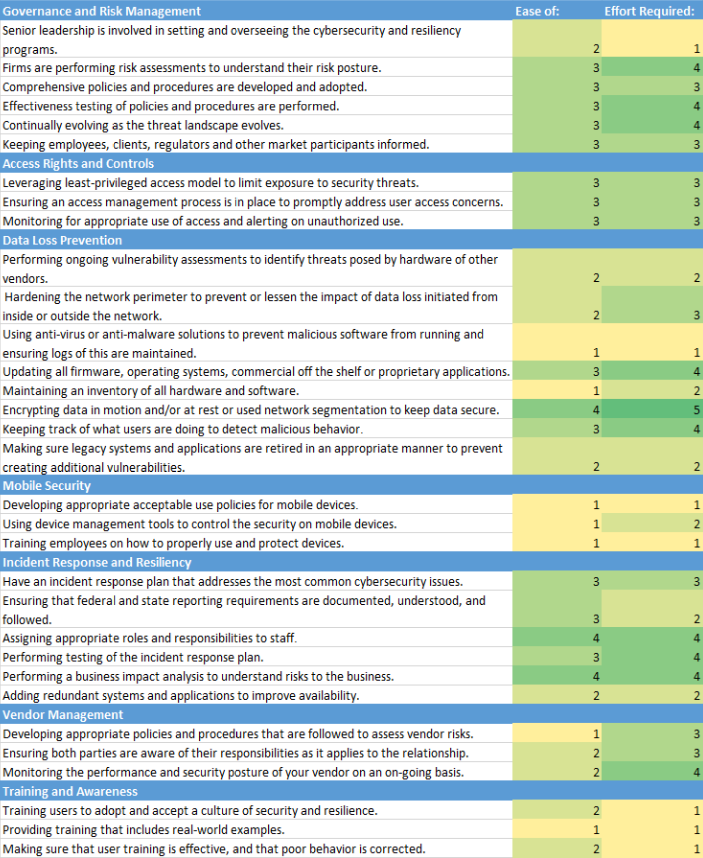
Governance and Risk Management
- Senior leadership is involved in setting and overseeing the cybersecurity and resiliency programs.
- Firms are performing risk assessments to understand their risk posture.
- Comprehensive policies and procedures are developed and adopted.
- Effectiveness testing of policies and procedures are performed.
- Continually evolving as the threat landscape evolves.
- Keeping employees, clients, regulators and other market participants informed.
Access Rights and Controls
- Leveraging least-privileged access model to limit exposure to security threats.
- Ensuring an access management process is in place to promptly address user access concerns.
- Monitoring for appropriate use of access and alerting on unauthorized use.
Data Loss Prevention
- Performing ongoing vulnerability assessments to identify threats posed by hardware, software or other vendors.
- Hardening the network perimeter to prevent or lessen the impact of data loss initiated from inside or outside the network.
- Using anti-virus or anti-malware solutions to prevent malicious software from running, and ensuring logs of this are maintained.
- Updating all firmware, operating systems, commercial off the shelf or proprietary applications.
- Maintaining an inventory of all hardware and software
- Encrypting data in motion and/or at rest or used network segmentation to keep data secure.
- Keeping track of what users are doing to detect malicious behavior
- Making sure legacy systems and applications are retired in an appropriate manner to prevent creating additional vulnerabilities.
Mobile Security
- Developing appropriate acceptable use policies for mobile devices.
- Using device management tools to control the security on mobile devices.
- Training employees on how to properly use and protect devices.
Incident Response and Resiliency
- Have an incident response plan that addresses the most common cybersecurity issues.
- Ensuring that federal and state reporting requirements are documented, understood, and followed.
- Assigning appropriate roles and responsibilities to staff.
- Performing testing of the incident response plan.
- Performing a business impact analysis to understand risks to the business.
- Adding redundant systems and applications to improve availability.
Vendor Management
- Developing appropriate policies and procedures that are followed to assess vendor risks.
- Ensuring both parties are aware of their responsibilities as it applies to the relationship.
- Monitoring the performance and security posture of vendors on an on-going basis.
Training and Awareness
- Training users to adopt and accept a culture of security and resilience.
- Providing training that includes real-world examples.
- Making sure that user training is effective, and that poor behavior is corrected.
How do you stack up against the observations provided by the OCIE? If you find gaps, you are not alone. We developed a matrix based on the observations mentioned in the OCIE alert. The purpose of the matrix is to provide you a realistic view of the ease and effort required to implement the observed policies and solutions. We understand this matrix does not apply to some firms, however, based on the data we collected and correlated over time (asset management firms from $150 million to $30 billion) this is what we have identified.
1-Minimal
5-Major
If you have questions related to this matrix, we would be happy to discuss it with you. We would also love to hear if you agree or disagree with our findings.



