FIND THE SECURITY ISSUES WITH OUR VULNERABILITY ASSESSMENTS
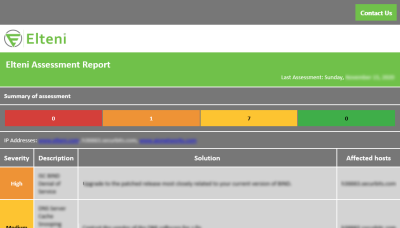
Elteni’s Vulnerability Assessments identify and rank the security issues present in our clients’ systems and network.
Vulnerability assessments are commonly performed by using automated testing tools that have been specially customized to assess an environment. This process discovers misconfigurations, unsupported or outdated software, missing patches, publicly disclosed exploits, and unintentionally opened ports and services to name a few.
Elteni provides actionable information to help you formulate a plan and remediate the risks.
All external vulnerability assessments are performed from our own servers. Internal assessments can be performed with Elteni’s Remote Penetester Device (ERPD). Elteni offers Vulnerability Assessments as a standalone service. Vulnerability scanning is also included in all of our external penetration tests and can be found bundled into some of our other offerings.
The Elteni consultants perform validation of the discovered vulnerabilities, excluding denial-of-service (DoS), and removes all false-positives.
THE POTENTIAL ENTRY POINTS
External
WHAT CAN BE COMPROMISED
Internal
ARE YOU STANDARDIZING
Configuration
HOW OFTEN DO YOU NEED ASSESSMENTS?
In need of an annual check-up? We have you covered.
Need to meet business or regulatory mandates? Let us help.
Need something more frequent? Of course you do!
Want to ensure you are not exposed? We can tell you!
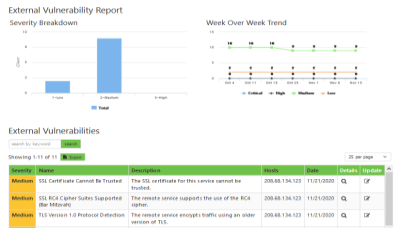
We provide you with automated email reports and data via our client portal so you can see the trends.